Cross-Chain Bridges
What are bridges?
Blockchain bridges (or bridges) are basically platforms that connect two different networks. They allow transfers of assets and information from one blockchain to another, expanding the possibilities for user interaction and solving one of the main problems of blockchains, the lack of interoperability.
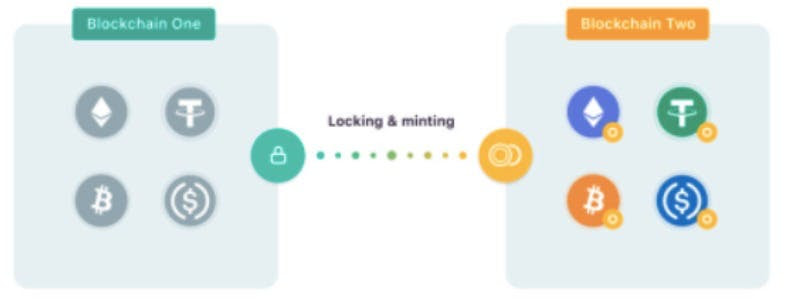
Blockchain tokens are often not compatible with each other, and bridges create synthetic derivatives that represent an asset from another blockchain.
Thus, cryptocurrencies and NFTs are no longer isolated in their native chains, and can be moved on different blockchains, multiplying the options for using these assets with each network.
For example: if you use a bridge to send a SOL token to an Ethereum wallet, that wallet will receive a token that has been “wrapped” or “wrapped” by the bridge – converted into a token based on the target blockchain.
In this case, the Ethereum wallet receives a “bridge” version of Solana that has been converted into an ERC-20 token – the generic token standard for fungible tokens on the Ethereum blockchain.
What types of bridge are there?
Bridges can be categorized according to their functions, mechanisms and levels of centralization. There are basically two types of bridges: custodial (centralized) and non-custodial (decentralized):
Custody bridges require users to trust a central entity to properly and securely operate the system. Users should do extensive research to ensure that this entity is trusted.
Non-custodial bridges operate in a decentralized fashion, relying on smart contracts to manage the blocking and transactional processes, removing the need to rely on a bridge operator. In this case, the security of the system depends on how secure the underlying code is.
One-way and two-way bridges
In a one-way bridge, users can only bridge to one target blockchain. It is not possible to do the reverse way, i.e. returning the token to the source blockchain.
In bidirectional bridges, the transfer of assets in both directions is allowed.
Benefits
The most important benefit of blockchain bridges is the ability to improve interoperability between networks.
They allow the exchange of tokens, assets and data on different blockchains, whether between layer 1 and layer 2 protocols or multiple sidechains. For example, WBTC allows bitcoin users to exploit the decentralized services (dapps) and DeFi of the Ethereum ecosystem. An interoperable blockchain sector is critical to the future success of the industry.
Another advantage is improved scalability. Some blockchain bridges can handle numerous transactions, improving efficiency, providing faster transactions at lower costs.
# Risks
According to data from Chainanalysis, an estimated over $2 billion in losses in 2022 alone is put on the table as a result of vulnerabilities in the DeFi ecosystem and the bridge industry.
Bridges are often an attractive target as they feature a central fund storage point that serves as a backbone on the receiving blockchain, regardless of how those funds are stored, whether locked in a smart contract or with a centralized custodian. That is, they establish a central point of all resources.
From a security point of view, the most reliable bridges are those platforms that rely on third parties to validate transactions, that is, they are not decentralized. Platforms that rely exclusively on smart contracts and asset custody algorithms are less secure bridges - in theory, because their security factor is more closely linked to the underlying network where the tokens/assets are being interconnected.
On the other hand, custody bridges can expose users to a centralized entity behind the custody, which can be negligent or steal user funds.
Main Bridges

Today, there are dozens of bridges in the crypto ecosystem, which are responsible for millions of dollars in crypto assets moved daily between the most diverse blockchain networks.
The outstanding protocols on the market are based on several networks, not exclusively being the result of Ethereum support, contrary to what one might imagine.
In 2022 alone, more than 10 hacks have already been carried out and many of them were connected with bridges.
Let's see the main ones:
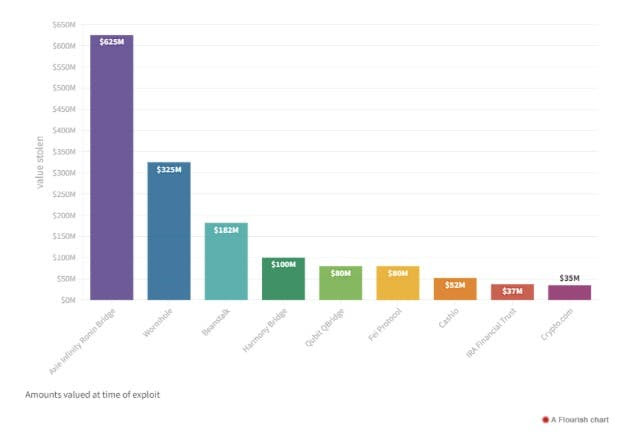
- Axie Infinity Ronin Bridge, March 28, was the victim of the second-biggest hack in the industry, with $625 million stolen when hackers gained control over most of the cryptographic keys protecting the bridge.
- Wormhole on Feb 2 had $325 million taken when a hacker exploited smart contracts on the Solana-to-Ethereum bridge to lie and withdraw in packaged ETH without posting collateral.
- Harmony Bridge, on June 23, had $100 million taken by the North Korea-linked Lazarus group, which accessed two of the bridge's five security keys Binance and Ethereum, approving transactions that divert assets from the bridge.
Ronin Bridge
Ronin bridge operates as a centralized bridge platform, using a multisig wallet for custody of assets, that is, it requires two or more cryptographic signatures to approve a transaction. In Ronin's case, the sidechain has nine validators that need five different signatures to approve deposits and withdrawals.
Despite the risk diversification strategies, the hack turned out to be the biggest hack of the year, taking over $625 million from the community. In the episode, March 23, four of the five required signatures were held by the Sky Mavis team alone, creating a single point of failure. After the hacker managed to control the four Sky Mavis subscriptions at once, only one more subscription was needed to approve the withdrawal of the assets permanently. The hacker managed to gain control over the Axie DAO signature, the final piece needed to complete the attack. 173,600 ETH and 25.5 million USDC were drained from Ronin's escrow agreement in two different transactions in the second-biggest attack ever to take place in the industry.
The Sky Mavis team discovered the hack almost a week later, showing that Ronin's monitoring mechanisms were deficient, revealing another flaw in the platform, which until then was considered trusted by the community.
Wormhole
Wormhole, a platform based on the Solana network that allows bridge transactions between Solana and Ethereum, was exploited in February, with more than $325 million stolen due to a bug in Solana's custody agreements.
A bug in Wormhole contracts, basically a code vulnerability, allowed the hacker to create bridge validators. The attacker sent 0.1 ETH of Ethereum to Solana, to trigger a set of “transfer messages” that tricked the software into approving an alleged deposit of 120,000 ETH.
Jump Crypto, the venture capital firm behind Wormhole, replenished the stolen funds to keep Solana-based platforms affected by the hack. Wormhole bounced back, renaming its bridge the Portal and currently holds more than $480 million, according to DeFi Llama data.
Nomad
Bridges work by locking tokens in a smart contract on one chain, and then re-issuing those tokens in a “wrapped” form on another chain. If the smart contract on which the tokens are initially deposited is sabotaged, the wrapped tokens will no longer have escrow support, which makes them financially useless.
That's what happened in the Nomad case, with more than $200 million stolen. A flaw in the contracts allowed the substitution of transactional addresses, with suspicions that a recent update to the protocol's smart contracts may have facilitated the spoofing of transactions by users, who could withdraw money from the Nomad bridge that did not actually belong to them.
Long Range Effects
The massive loss of resources in a bridge is not the biggest problem that hacks in this segment can generate. Extensions can be much larger.
The fact that bridges cover and connect to different networks and platforms, expands the effects of losses to more than one point in the ecosystem, making the situation more complex.
By creating interrelationships between blockchains, bridges make the assets “wrapped” in different blockchains spread out, making it more difficult to locate the original asset that backed the asset wrapped in other networks.
That is, a successful attack on a cross-bridge can cause a particular asset to be devalued on a specific platform it is natively linked with, for example, but not on others, creating significant arbitrage opportunities for hackers to extract. value from other networks.
Interoperability is an essential theme for the evolution of blockchain technology and for the future of the crypto industry, as it tends to increase the adoption of crypto assets.
Bridges provide a great advance for interoperability, but still need improvements in terms of security, however, they are an important part of the evolution of WEB 3.
Posted Using LeoFinance Beta

https://twitter.com/CryptoSimplify/status/1557720219967115264
The rewards earned on this comment will go directly to the people( @cryptosimplify ) sharing the post on Twitter as long as they are registered with @poshtoken. Sign up at https://hiveposh.com.
Yay! 🤗
Your content has been boosted with Ecency Points, by @cryptosimplify.
Use Ecency daily to boost your growth on platform!
Support Ecency
Vote for new Proposal
Delegate HP and earn more
This post has been manually curated by @bhattg from Indiaunited community. Join us on our Discord Server.
Do you know that you can earn a passive income by delegating your Leo power to @india-leo account? We share 100 % of the curation rewards with the delegators.
Please contribute to the community by upvoting this comment and posts made by @indiaunited.