Guide On How To Secure Your Cryptocurrency Wallet

The coming of decentralized wallets (Non-Custodian Wallets) was welcomed with opened hands in the crypto space because it solved the problem of users losing their funds when a centralized exchange is hacked. Just as it is in nature, everything that has merit will surely have its demerit.
Decentralized Wallets were built in such a way to offer wallet access to the owner alone, sadly with the existence of Fraudulent Smart contracts, clone extensions of decentralized wallets, etc, the security of Decentralized wallets became a challenge for investors.
In this post, I will try as much as possible to point out possible ways by which the Security of a Decentralized wallet can be lost and possible ways to prevent it.
INTERACTION WITH A FRAUDULENT SMART CONTRACT
For Defi projects to offer decentralization to users, it incorporated the use of Smart Contracts. Smart contracts are self-executing contracts which makes it possible for a transaction that meets up to the conditions written in the codes which make up the smart contract to be executed.
For one to be able to interact with the smart contract, certain privileges are being granted to the Smart contracts. This permission can be limited or unlimited base on the codes guiding the smart contract.
Bad players will always exist in the digital world. Scammers started coding smart contracts in such a way that permitting the Smart contract call ( during sell or buy ) gives them the unlimited privilege to spend funds with or without your permission. If one falls victim to such a contract, the chances of losing his entire wallet balance are very high. This is how some people have woken up to empty wallets.
Solution
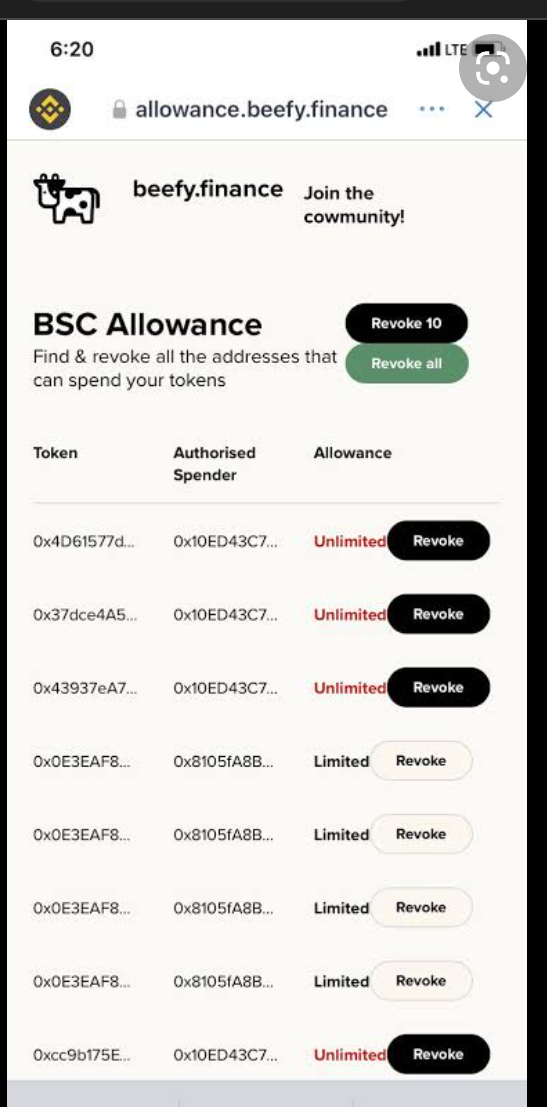
Beefy finance has been able to build a counter smart contract that can reveal the degree of permission given to all the smart contracts you have interacted with.
All you need to do is to log in to https://allowance.beefy.finance/ through your Dapp and you will be able to see the list of smart contracts and the degree of permission they have. A sample is shown below. You should do this for all the networks you have interacted with.
NB: I used an image from the internet because I have Revoked all the smart contracts I have interacted with, this there is nothing to display in my wallet.
CLONE WALLET EXTENSION FROM SCAMMERS
Web3 wallets like Metamask and Trust wallet are not used directly on PCs, one needs to download the extension. Scammers have built a similar extension but with a different code that returns the user's private keys to them when a user inputs his or her private keys.
Solution
Always download extensions from the official site of Metamask and other wallets you want to use.
STORING YOUR PRIVATE KEYS AS DOCUMENTS ON YOUR PHONE AND GIVING PERMISSION TO APPS TO ACCESS YOUR DOCUMENTS.
Most apps always demand access to galleries and documents on the phone. When one stores his recovery phrase on his phone, fraudulent apps that have permission to your documents can steal the information within. This puts your wallet at great risk.
Solution.
If you must store your private keys on your phone, then you should adopt the pattern of rearranging the position of any two of the words BUT ENSURE YOU REMEMBER THE RIGHTFUL POSITIONS OF THESE WORDS because you stand the chance of losing the wallet if you can't place them back at their right full position. The best practice is to write them down in your journal where no other party can access them.
HAVING ALL YOUR FUNDS IN THE SAME WALLET THAT YOU USE ON DEX.
When we have our eggs in one basket, then we are likely to lose them if there is a hack on lie wallet.
Solution.
Endeavor to have a separate wallet for tokens you want to hodl for a longer period, and a separate one for coins you are trading with.
OTHER GOOD PRACTICES THAT CAN HELP SECURE YOUR WALLET
- If you are using Trustwallet, ensure that you enable Transaction signing. This makes it possible for transactions to be confirmed through passwords or fingerprints as the case may be. To do this follow the images below.
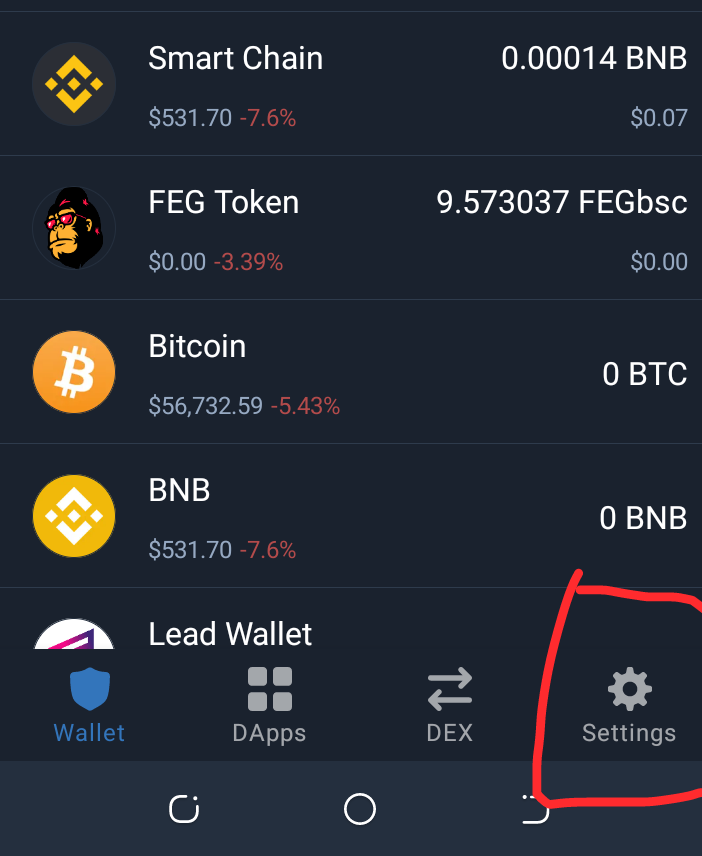
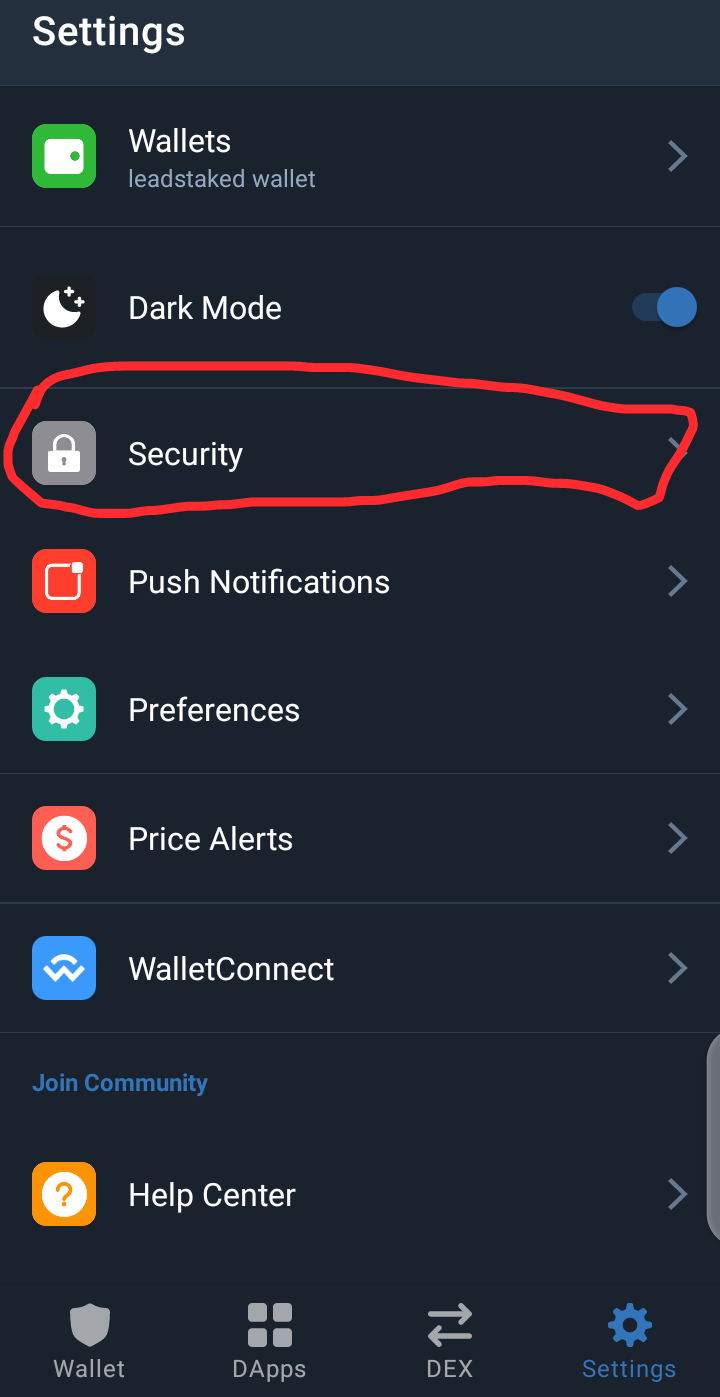
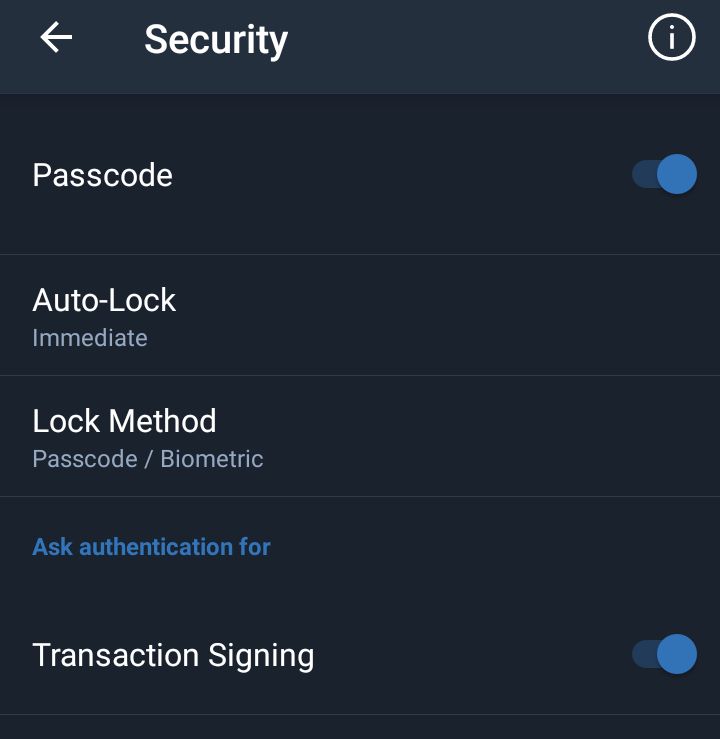
- Always disconnect from any Dapp after each transaction. For those using Metamask wallet, The guide for disconnecting from Dex after the connection is below.
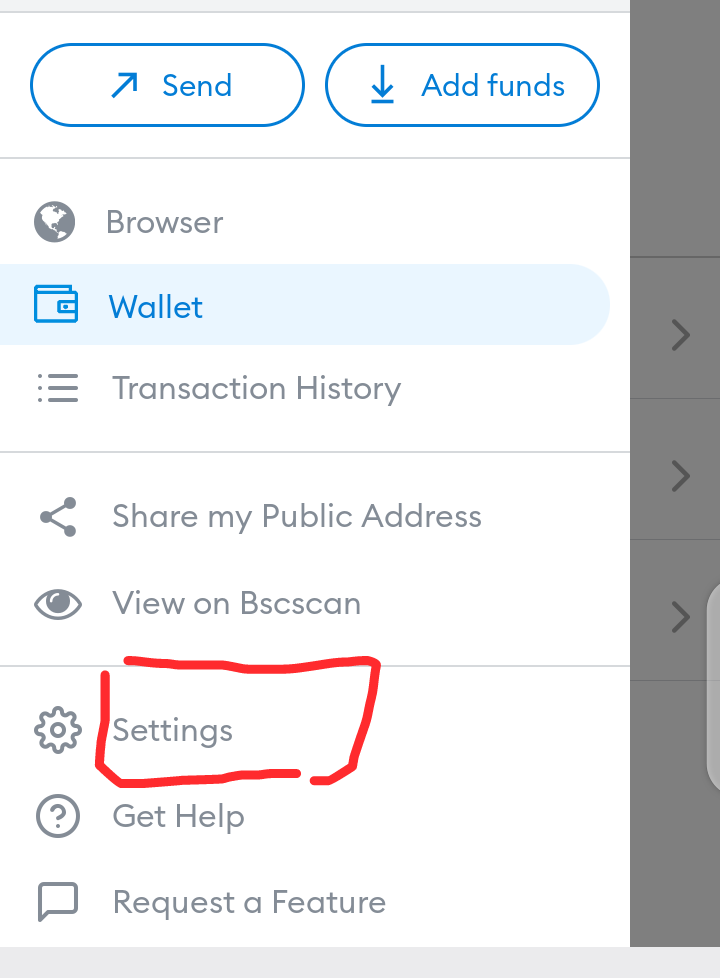
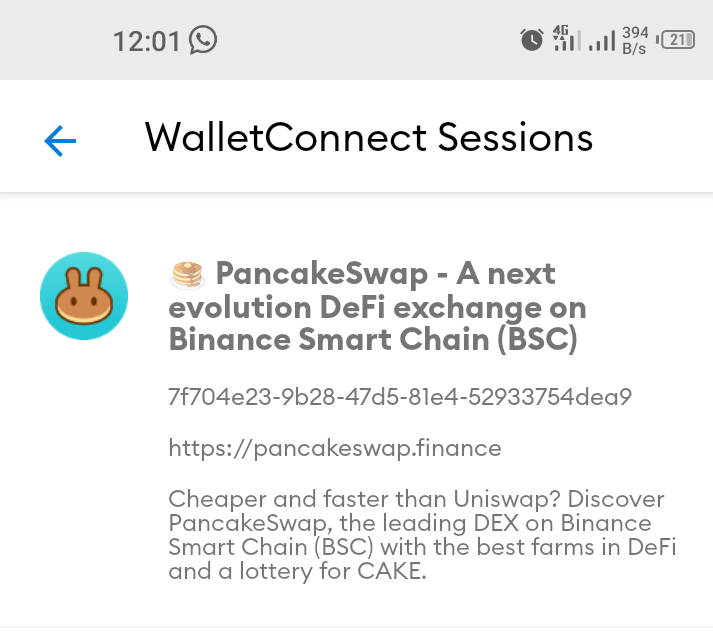
Now hold the DEx that showed up ( mine is the pancakeswap you are seeing) for few seconds, you will see a prompt asking you to end the session.
When downloading Decentralized wallets from PlayStore, ensure you download the ones that are verified by PlayStore.
Split your funds into two different wallets so that you won't lose all should anything happen accidentally.
N.B The last subtitle on other ways of securing your wallet are personal opinions, they are not laid down standards.
https://twitter.com/Josemendez_1010/status/1461574480753577990
The rewards earned on this comment will go directly to the person sharing the post on Twitter as long as they are registered with @poshtoken. Sign up at https://hiveposh.com.
Your content has been voted as a part of Encouragement program. Keep up the good work!
Use Ecency daily to boost your growth on platform!
Support Ecency
Vote for Proposal
Delegate HP and earn more