IT Auditing Series - Linux
Hello Everyone!
This post marks the second entry into my IT Auditing Series. Today we will be focusing on Linux, most specifically, Red Hat. Many of the concepts discussed are applicable to other distributions but generally each distribution has slight variations in the naming convention of the file structure.
This series and guide is intended for those of you just starting out in IT operations, IT compliance, and IT audit. We will be focusing on IT General Controls which generally cover Authentication, Authorization, and Change Management.
That said lets jump straight into the risks and control areas.
Authentication
Risk: IT infrastructure and applications are not configured to restrict system access to properly authorized users.Control: Authentication is restricted via unique IDs and passwords and other methods which validate access to systems is appropriate.
For Authentication controls we are primarily talking about setting systems to enforce strong password requirements. Linux enforces some basic restrictions by default and has multiple standard files which contain the relevant settings. Most notably the etc/login.defs file and the etc/pam.d/system.auth file. As noted above these files may vary slightly in name but ultimately all contain the needed settings.
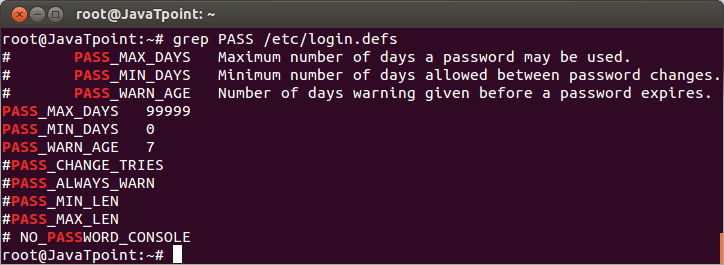
Image from javaTpoint.com
For login.defs there are two primary settings which impact passwords:
- PASS_MIN_LEN (Minimum length required for password)
- PASS_MAX_DAYS (Maximum number of days the password is valid)
Both of these files should be configured to meet company standard but best practice would require at minimum a length of 8 and max age of 1 year. Generally end users should be even less at around 90 days.
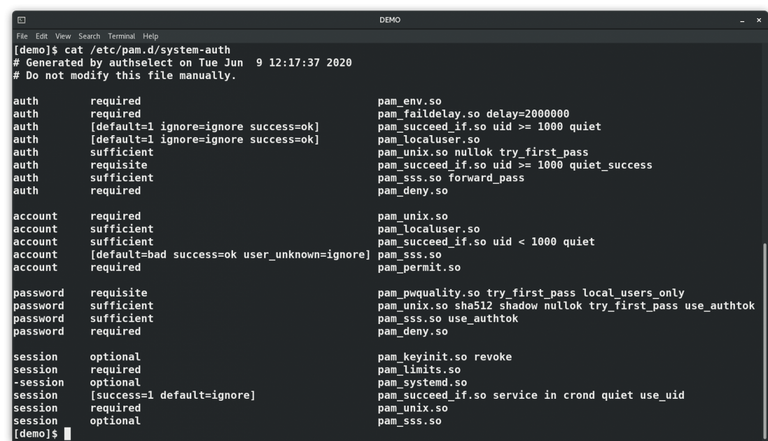
Image from RedHat.com
The PAM files are related to an optional PAM module. PAM or Pluggable Authentication Modules is a collection of pre-built utilities that allows admins to configure advanced authentication settings. Some of the most popular modules include: pam_cracklib and pam_pwquality. Both of these utilities provide additional password requirements such as common dictionary checks, password character requirements (num/Dig/Upp/Low), and password reuse history. These should also be configured to follow corporate policy but best practice is to configure the utilities to enforce at minimum 3 of the 4 character classes.
PAM can also be used to "link" the Linux environment to Active Directory in order to utilize Windows groups and users. Common utilities/applications which serve this purpose include vas and Centrify.
It is also generally best practice to lock or reset the default passwords of pre-built service IDs. This can be done using the etc/shadow file. For those completely new to Linux the shadow file contains a hash of each account's password. When a user attempts to login to Linux the system will hash the entered password and compare it to the hash in the shadow file. A match will authenticate the user and a mismatch will fail the auth attempt. Generally changing the hash or replacing the hash with a ! or other character such as LK, NP, etc, effectively locks an account from being interactively logged into.
Possible vendor default IDs include but are not limited to the follow: root (0), daemon (1), bin (2), sys (3), adm (4), lp (71), uucp (5), nuucp (6), smtp (25), webservd (80), gdm (50), listen (37), nobody (60001), noaccess (60002), nobody4 (65534).
Authorization
Risk: Users have access beyond what is needed to perform their duties.Control: Restrict access based on the Least Privilege Access principle. Access should be approved and justified prior to grant.
Privileged access in the Linux environment is most closely associated with the root ID. Regardless of the distribution which you are using this is the default admin account and it controls and has access to everything.
Management of this account and accounts given root-like access is critical. This area in particular is one of the challenges in Linux compliance as there are many different routes to assigning root-like access including:
- Assigning users to the root group. GID (0)
- Assigning an ID the root UID (0)
- Assigning an ID sudo access to root or providing sudo ALL access
As this type of access can be nested it is important to inspect and configure all related files appropriately: etc/passwd, etc/group, etc/sudoers, etc/sudoers.d. It is also advisable that write access to these files is also specifically restricted to root.
Change Management
Risk: Inappropriate or unapproved changes are made to the IT environmentControl: IT changes should be tested, documented, and approved prior to production implementation.
Generally the Linux change process should follow the same process as any other IT environment and should include a change request, approval, documentation of testing, and appropriate justification. Most system changes can be identified by the following command: rpm -qai. It can further be filtered to pull changes by date and other qualifiers. When ensuring compliance to the change process, a selection of these changes should be sampled and traced to the change documentation.
Post Tax

Those that follow me are aware I also adhere to the internet tax, ie pet pictures. For today's tax, I give you Nobu's watchtower. This is his favorite position to hang out in whenever I'm cooking dinner or in the family room. Always with that front paw just chillin.
All images and content owned by me unless otherwise noted.
Helpful Details
Monster CuratorFor those of you that blog, consider delegating your SPT to @monster-curator for daily SPT payouts. For more information checkout their how-to post here.
Hive Basic Income (HBI)
HBI is effectively an automated curation tool which will upvote your HIVE posts forever. It is an amazing way to ensure you get some income from all of the time you spend teaching others via posting your strategies, analysis, and thoughts. You can read more about HBI in their FAQ.
Support
If you are new to the Crypto space and wish to support Atlas, Nobu, and myself, please utilize the following referral links. You can also support me via Tip directly through Hive or including my name in a HBI purchase.Exchanges
Coinbase - $10 signup bonus
Bittrex
BlockFi - $10 after funding $100
NFT Games
Splinterlands
Gods Unchained
Exode - 2 free alpha booster packs
Rising Star
nice post
I like Linux and every time I see a terminal like this I just love it ahahah I may be crazy but that's just the way I am, I rather do "ls" on the terminal than see the files in the folders the desktop way ahahahah
Nice post! 😎 Dropped you a follow
Oh and lovely cat! :) Say hi to Nobu from me!
Very technical and informative post. Having just converted an older laptop from Win10 to Linux the first thing I noticed was the DOS-like UI of the Terminal. Back in the day, I used to do little DOS things, not anymore.
I really like seeing you pay your internet tax, especially in such a cute manner. That front paw 😍
Also, I didn't know you got into Exode. I own a planet there, too, but haven't played it in a while.
Yeah, Linux is all about that terminal :P This post likely didn't help you too much in terms of day to day use of a personal machine. I might have to put together a beginner users guide too. Things like basic navigation commands etc. Terminal use is definitely not that common in the general public.
Exode seems like a game that will 100% be in my niche in the future. I've always liked space themed things. Board games, video games, classes, etc. I'm still new to it and have only done a few rounds of extraction. I can't wait for the game to continue to develop.
Correct, it didn't help me personally, but it's still a good post.
There are a lot of 'beginner' Linux posts out there, and they helped me got this machine up and running, but it wasn't all easy. So, if you come up with a post... I'll be here